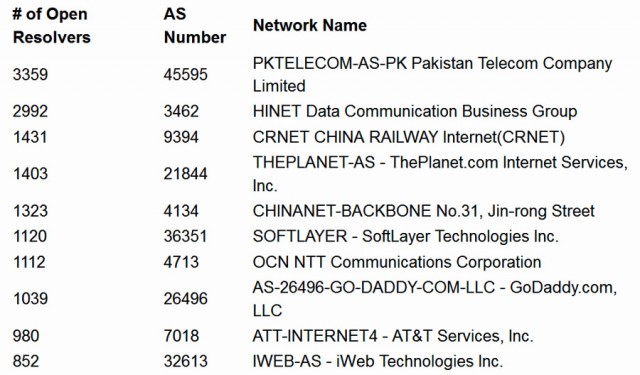
Enlarge / A list of the the 10 network operators with the highest number of open DNS resolvers, as measured by CloudFlare. Over the past three weeks, third-party attackers have been abusing them around the clock in an attempt to knock a website offline.
A company that helps secure websites has compiled a list of some of the Internet's biggest network nuisances—operators that run open servers that can be abused to significantly aggravate the crippling effects of distributed denial-of-service attacks on innocent bystanders.
As Ars recently reported, DDoS attacks have grown increasingly powerful in recent years, thanks in large part to relatively new tools and methods. But one technique that is playing a key role in many recent attacks isn't new at all. Known as DNS amplification, it relies on open domain name system servers to multiply the amount of junk data attackers can direct at a targeted website. By sending a modest-sized domain name query to an open DNS server and instructing it to send the result to an unfortunate target, attackers can direct a torrent of data at the victim site that is 50 times bigger than the original request.
Engineers at San Francisco-based CloudFlare have been shielding one customer from the effects of a DDoS attack that has flooded it with 20 gigabits-per-second of data around the clock for three weeks. While attacks of 100Gbps aren't unheard of, that's still a massive attack even large botnets are generally unable to wage.
Read 13 remaining paragraphs | Comments
DIGITAL JUICE
No comments:
Post a Comment
Thank's!