First, let me start that if you want a lot of people to download something, make sure that the words "HTML5," "Support" and "Update" appear in the title. I'm sure if the folks that are making Diablo 3 called it "Diablo 3 HTML5 Support Update" that a metric buttload more people would download it.
That said, a bunch of folks in the Web Platform and Tools team created the Web Standards Update package with HTML5 Support for the Visual Studio 2010 Editor.
This Web Standards Update is something that anyone in the community could have released, just extending Visual Studio in a standard way. Like many other (most) extensions in Visual Studio Extension Gallery, it was not "signed." It was not a formal project done by Microsoft. Ratherthis was something that a bunch of us did for the community in our after work hours. The only reason why this got in spotlight was because press caught the wind of it having HTML5 and CSS3 support.
Certainly a lot of people wanted it because in 4 days it's now the #1 most popular thing in the Visual Studio Gallery. Take that NuGet! ;)
Here's where the trouble starts. Then, it was written about in the press as if it were a "gaffe." I admit that we (mostly I) did a lousy mediocre job of making it clear that this update was a "community update from the inside," as it were. It's not official, but we're hoping support like this will make its way into the next version of Visual Studio.
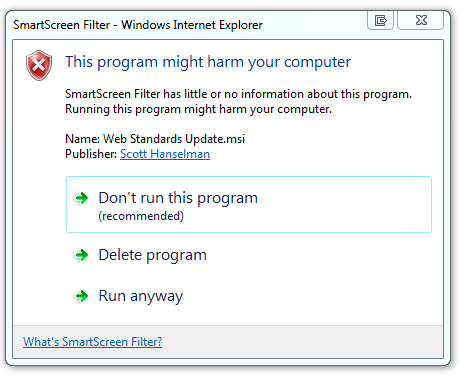
When you downloaded the MSI installer with IE9, as with all MSIs that aren't signed, you get a message like this:
And that's normal and quite lovely. Then we see this scary red bar (this is a shot from another gallery item):
This is the IE9 SmartScreen system warning us, rightfully so, that this is not something downloaded all the time. In fact, this is a really useful feature of IE9 and is fairly unique amongst the browsers so far. It's using some special sauce (some hash, some math, some metrics) to make a non-biased judgment about this download. Even though it's coming from a Microsoft.com website it doesn't matter. SmartScreen is unbiased. It's never seen this before, and it's not trusted.
UPDATE: Looks like as of my test just now that SmartScreen now recognizes our download as safe!
At this point, if I click Actions, I see this. (Yes, I realize these screenshots aren't all up to snuff).
_9a12330c-2264-49f0-8d29-bbd55f7ffb0a.png)
In fact, for most people, they can't even click "Run Anyway" yet. They'll have to click More Options to see the Run Anyway button. (If I am a developer-type and click More Options all the time, presumably I either know what I'm doing, or I like to live dangerously and the More Options choice will stick open after several downloads. It'll save me a click, but all the other warnings remain.)
As the publisher, we have a few choices. We could sign the binary file (the MSI) with the Microsoft code certificate. However, that requires a big manager to sign off and says explicitly that Microsoft is releasing this code officially. It's a big deal. This wasn’t an official release and as such, we can't sign it as Microsoft. A code signing certificate guarantees that a file hasn't been tampered with and that a known and verified organization or individual stands behind it.
Eventually SmartScreen would figure out that our MSI was OK, but we have no way of telling how long that would take. Could be weeks, months, it all depends. Regardless, the right thing to do is to sign your code, even if you are an individual or small company. For example, if I download Eric Lawrence's Fidder or Rick Brewster's Paint.NET, they are both signed and I can see their names in the User Account Control (UAC) dialog. I can click and view their certificates and know I'm downloading a file that has someone vouching for it.
Be sure to check out Eric Lawrence's excellent post on Authenticode Code Signing. It's extremely detailed and worth your time.
Getting a Code Signing Certificate
I got a Code Signing Certificate from InstantSSL.com. There's many options, they are one. It's spendy, $180 a year, or $166 a year if you got for 3 years, but I can use it for other stuff.
There's a few gotchas in the process, no matter who you pick.
- Use the same computer, same OS, and same browser (preferably IE, for this, no joke) when you sign up for the certificate. That's because half the certificate (a cert request cert) comes down when you request a certificate and they match them up when you actually get the certificate.
- Have P.O. Box, corporate address or ask them via tech support to remove your address. Otherwise your full details may get embedded in the cert.
- You'll need to prove who you are. More on that now.
You'll need to prove you are really you. I needed to give their verification people a copy of the first page of my passport, driver's license, two utility bills, including phone whose address matched my credit card's address, AND they called the phone number on my utility bill to confirm it was really me. It's non-trivial, it takes a while, and they aren't screwing around. Good for you, the consumer, hassle for me, the producer. Still, good stuff.
_3.png)
When my cert shows up, I need to Export it and save it in a safe place with all its details and a strong password. It's unique and should be protected.
Signing Code
The actual signing, once the cert shows up is not too hard. Here's a command line used with the signtool.exe that came with Visual Studio. You can also download it separately.
C:\DEV> signtool sign /t http://timestamp.comodoca.com/authenticode /f "C:\DEV\HanselmanCODESIGNINGCERT.pfx" /p SecretPassword '.\MySpecial.msi'
Done Adding Additional Store
Successfully signed and timestamped: .\MySpecial.msi
When someone tries to download the new signed MSI, they see this slightly less scary yellow bar. What? I don't get a free pass for signing my code?
Well, just like getting an SSL certificate doesn't make me a bank, getting a Code Signing Certificate doesn't make me more trustworthy.
- SSL Certificates for HTTPS guarantee privacy, not trust.
- Code Signing Certificates guarantee identity, not trust.
- It guarantees it's me, but you have to decide if you trust me.
If you click Actions now, you'll see my name as the Publisher, and you can validate the certificate and decide if you trust me. But SmartScreen doesn't trust me yet. Why?
That's because my Certificate, unlike the Microsoft one, hasn't built up a reputation*. The "Scott Hanselman" code signing cert will have to earn trust, just as Rick Brewster and Eric Lawrence and every other signed shareware or freeware author has built trust. But, having this MSI signed means you now that I (and Mads, and Vishal, and the folks working on this MSI) stand behind it. Hopefully soon (some # days or weeks vs. downloads?) SmartScreen will trust us also, and this will make future projects I sign be trusted faster. At that point, my signed code will be trusted and SmartScreen won't frighten you with this download.
Remember also that code signing certificates and the Windows experience and UI for running signed MSI and EXEs is a separate from SmartScreen. They work together and compliment each other though. Learn more about SmartScreen on their team blog or their FAQ.
Hope this helps! Surf smart, and think about what you download and who you trust.
* Now it appears that SmartScreen trusts me!
© 2011 Scott Hanselman. All rights reserved.
No comments:
Post a Comment
Thank's!