The Flashback ad-clicking component is loaded into Chrome, Firefox, and Safari where it can intercept all GET and POST requests from the browser. Flashback specifically targets search queries made on Google and, depending on the search query, may redirect users to another page of the attacker's choosing, where they receive revenue from the click . (Google never receives the intended ad click.)
Symantec's work on the ad-click hijacking aspect of Flashback comes after Russian firm Dr. Web, which was responsible for the initial publicity about the malware, published its own report examining some of the early data on infected computers seeking to connect to command-and-control servers.
The report looks at nearly 100,000 connections that came in on April 13, finding that close to two-thirds of the infected machines identified themselves as running Mac OS X Snow Leopard, which was the last version of OS X to ship with Java enabled by default. OS X Lion does not include Java by default, and thus was responsible for only 11% of infections seen during the survey period.
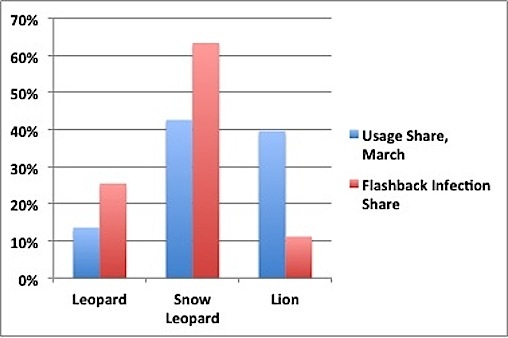
Flashback infection share vs. operating system usage share (Data via Dr. Web, Chart via Computerworld)
As noted by Computerworld, OS X Lion represents nearly 40% of OS X copies currently in use, suggesting that Apple's decision to remove Java from the default Lion install is indeed helping to limit infections on Apple's newest machines.
[W]hile Snow Leopard's and Leopard's infection rates are higher than their usage shares, the opposite's true of OS X 10.7, or Lion. The 2011 OS accounted for 39.6% of all copies of OS X used last month, yet represented only 11.2% of the Flashback-compromised Macs.
Dr. Web's data on OS kernel versions being reported from infected Macs also demonstrates that many Mac users do not keep their systems up-to-date, with roughly 25% of Snow Leopard and Lion systems seen in the survey reporting themselves as at least one version behind Apple's most recent updates (10.6.8 for Snow Leopard and 10.7.3 for Lion).
Recent Mac and iOS Blog Stories
• Apple's New Highland Village Retail Store in Houston Hit by Gunfire
• Upcoming Saskatchewan Apple Retail Store Fills Huge Void in Coverage [Updated]
• Scott Forstall and Mickey Drexler Net Millions in Apple Stock Sales
• Apple Temporarily Closing Some U.S. Stores for Security Grate Installations
• Apple "Discussed" Putting a Hardware Keyboard on the iPhone
ICT4PE&D
No comments:
Post a Comment
Thank's!